
Okta has admitted that it made a mistake delaying the disclosure of hack from the Lapsus$ data extortion group that took place in January.
Additionally, the company has provided a detailed timeline of the incident and its investigation activities.
Okta: “we made a mistake” over late breach disclosure
On Friday, Okta expressed regret for not disclosing details about the Lapsus$ hack sooner and shared a detailed timeline of the incident and its investigation.
The hack from the Lapsus$ data extortion group originated at Sitel, Okta’s third-party provider of customer support services.
“On January 20, 2022, the Okta Security team was alerted that a new factor was added to a Sitel customer support engineer’s Okta account. This factor was a password,” explains Okta.
“Although that individual attempt was unsuccessful, out of an abundance of caution, we reset the account and notified Sitel” who further engaged a leading forensic firm to perform an investigation.
.jpg)
“We want to acknowledge that we made a mistake,” states Okta, further admitting that it is ultimately responsible for its contracted service providers like Sitel.
Okta claims that in January it wasn’t aware of the extent of the incident which, the company believed, was limited to an unsuccessful account takeover attempt targeting a Sitel support engineer.
Sitel’s engagement of a forensics firm for investigating the incident and preparing a report further provided assurance to Okta at the time that the matter required no further escalation.
“At that time, we didn’t recognize that there was a risk to Okta and our customers. We should have more actively and forcefully compelled information from Sitel. In light of the evidence that we have gathered in the last week, it is clear that we would have made a different decision if we had been in possession of all of the facts that we have today,” says Okta.
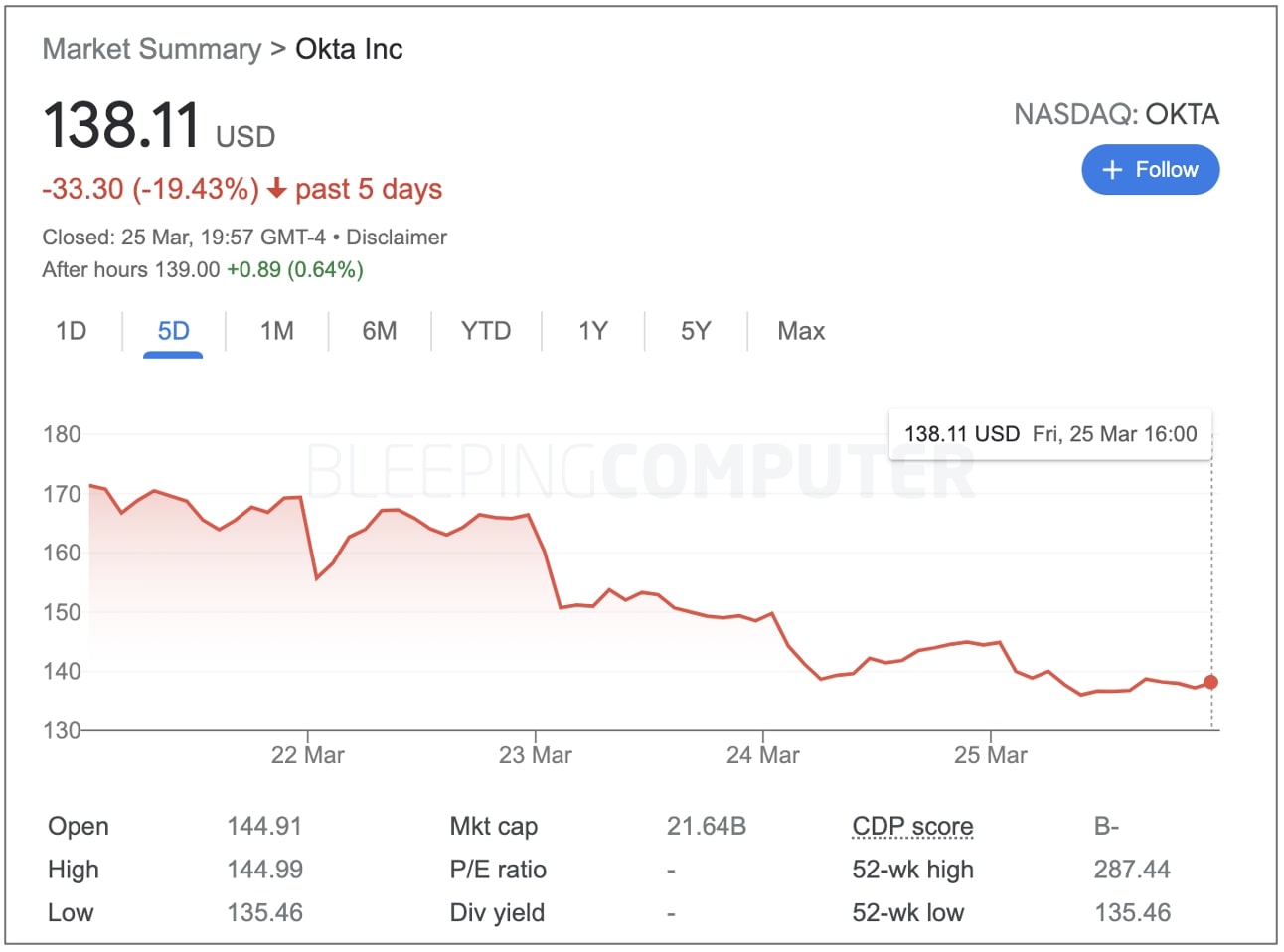
Okta’s shares fell by almost 20% after disclosure
Following Okta’s haphazard disclosure of the January cyber incident this month, the company’s stock price dipped by almost 20% in less than a week:
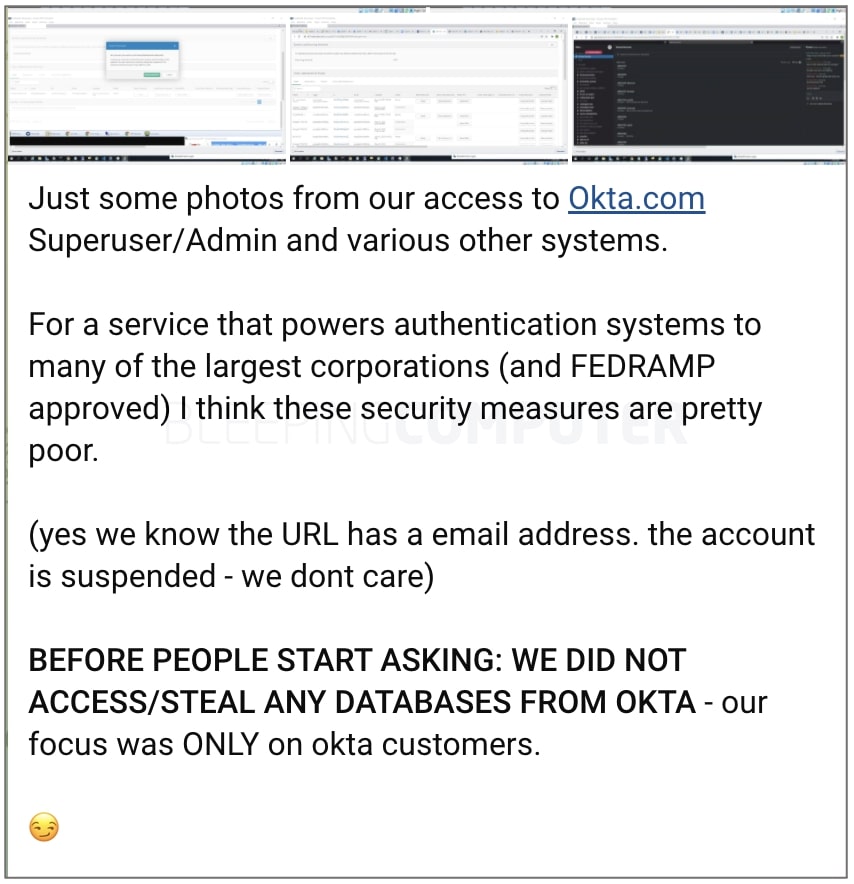
As reported by BleepingComputer this week, Okta had previously stated it was investigating claims of a hack after Lapsus$ members shared several screenshots in a Telegram chat implying they had hacked Okta’s customer networks:
Initially, Okta’s CEO Todd McKinnon labeled this incident an “attempt” by threat actors to compromise the account of a support engineer. However, it later became clear that 2.5% of Okta’s customers—366 to be exact, were indeed impacted by the incident.
The hack spanned over “a five-day window” between January 16th and 21th, during which an attacker obtained Remote Desktop (RDP) access to a Sitel support engineer’s laptop.
Fortunately, Sitel’s support engineers, according to Okta, have limited access to Jira tickets and support systems but are restricted from downloading, creating, or deleting customer records.
“Support engineers are able to facilitate the resetting of passwords and multi-factor authentication factors for users, but are unable to choose those passwords,” explains Okta.
In other words, support engineers can repeatedly trigger password resets for users but are unable to log in to user accounts.
Okta concludes that the screenshots shared by Lapsus$ group were taken from the Sitel engineer’s compromised account that had limited access.
The company also refuted Lapsus$ group’s claim of obtaining “superuser/admin” access, clarifying that the access obtained by Lapsus$ remained limited to an internal Okta support tool and is not synonymous with “superadmin” access that gives complete access to all users and system assets.
The application used by Sitel engineers is built with “least privilege in mind” to ensure that support engineers have only the specific access they require to perform their roles, explains Okta.
Regardless, the company expressed disappointment for the extended time it took for the investigation results to come out:
“I am greatly disappointed by the long period of time that transpired between our notification to Sitel and the issuance of the complete investigation report,” said David Bradbury, Okta’s Chief Security Officer.
“Upon reflection, once we received the Sitel summary report we should have moved more swiftly to understand its implications.”
It’s been a busy week for Okta’s security teams who spent hours analyzing more than 125,000 log entries to arrive at an authoritative picture of the cyber incident that occurred two months ago.
“As with all security incidents, there are many opportunities for us to improve our processes and our communications. I’m confident that we are moving in the right direction and this incident will only serve to strengthen our commitment to security,” concludes Bradbury.
