Many consider access control an essential component of cyber and information security – and for good reason. It’s one of the most basic steps you can take to protect your sensitive data, as well as one of the most versatile.
Access control means you’re limiting access to a place or resource to secure that asset. You’re putting controls in place such that only authorised individuals (or resources) can access that resource.
In this blog
How does access control work?
In their most basic form, access controls determine who may access certain data or systems, and what type of access they get (for example, view vs edit rights). They then restrict anyone else from accessing it.
Ideally, your access control should cover IAAA:
- Identification – identify someone by, for example, name, username or ID number.
- Authentication – verify their identity by getting them to, for example, enter a password or PIN.
- Authorisation – grant that person/resource the requested access.
- Accountability – trace individual account activities, and ensure non-repudiation. In other words, make sure you can prove which actions were performed by what accounts, in case you need to investigate a security event.
Broadly speaking, access controls follow a two-step process: an authentication mechanism followed by authorisation.
But for them to be effective, you must properly restrict access to information and systems – there can’t be another way of gaining access. You must also combine technical controls with strong access control policies.
Why is access control important?
Access controls significantly reduce the risk of an information security breach. Whether such a breach is deliberate or unintentional, access control helps address the insider threat, preventing unauthorised:
- Changes;
- Data transfers; and
- Information deletion.
By extension, if a threat actor gains control of a user account, you limit how much confidential or sensitive information they can access. This reduces the impact of a data breach.
Further reading: If you’re interested in taking access control one step further, you can learn about zero-trust architecture in this interview with information security manager Adam Seamons.
How to implement access control
You can implement access control in both the physical and digital world. For example:
- A physical access control might be an RFID (radio-frequency identification) reader that scans an employee’s identification card to permit them access to the building.
- A digital (or ‘logical’) access control might be password protection or MFA (multifactor authentication).
For both, you should follow two key security principles:
- The ‘need to know’ principle – granting users access to only the information they need to perform their job effectively.
- The principle of least privilege – granting users only the privileges necessary to perform their role effectively.
For example, most staff don’t need access to HR or financial data. In turn, an HR employee doesn’t need to be able to edit firewall settings.
Also ensure staff use administrative accounts for administrative tasks only. So, if an IT administrator needs to change the firewall settings, or change a device’s configuration, they should use their admin account.
But for day-to-day tasks like answering emails, they should use a standard user account. This minimises the risk of a threat actor gaining access to an administrative account.
Finding this blog useful? To get notified of future
content like this, subscribe to our free weekly
newsletter: the Security Spotlight.
Legal and best-practice requirements
Access control is a common security measure, designed to protect primarily the confidentiality and integrity of information.
And as low-hanging fruit, access control is a good place to start for meeting legal requirements like Article 32 of the GDPR (General Data Protection Regulation), which demands “appropriate technical and organisational measures” to ensure data security.
‘Integrity and confidentiality’ is also one of the Regulation’s key data protection principles.
Plus, access control is an explicit requirement in best-practice security frameworks ISO 27001 and Cyber Essentials.
ISO 27001 requirements for access control
‘Access control’ is one of the Annex A controls (control 5.15) in ISO 27001. Control 5.15 states:
Rules to control physical and logical access to information and other associated assets shall be established and implemented based on business and information security requirements.
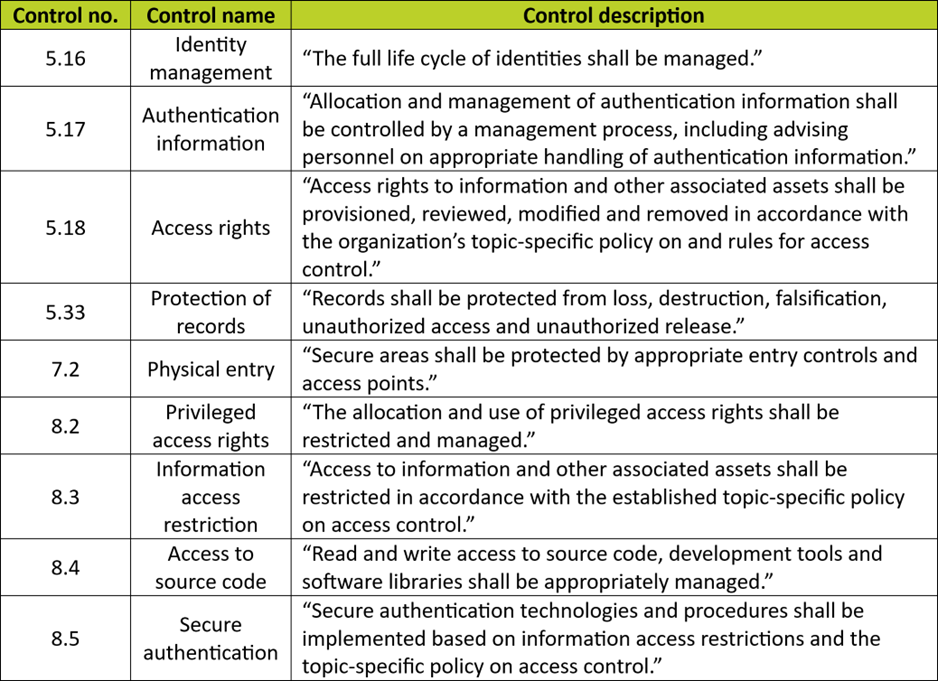
Various other controls in Annex A also relate to IAAA, including:

This blog doesn’t have room to go into detail for each control, but this list highlights just how many areas of security may require access control.
The idea behind the controls in ISO 27001 and ISO 27002 isn’t to be exhaustive or prescriptive, but to provide a selection of security measures that may or may not apply to you. It’s designed to help organisations not accidentally overlook any security categories that may apply to them.
For example, you’re not just restricting access to digital information – you also want to control physical access. You may also want to take extra precautions with more sensitive information like source code.
Cyber Essentials requirements for access control
Cyber Essentials is a UK government-backed scheme intended to help organisations protect themselves from common, low-level cyber threats with five basic control themes, including user access control.
Further reading: This blog explains the key differences between Cyber Essentials and ISO 27001.
The Cyber Essentials requirements state:
Your organisation must be in control of your user accounts and the access privileges that allow access to your organisational data and services.
[…] this also includes third party accounts – for example accounts used by your support services.
You also need to understand how user accounts authenticate and manage the authentication accordingly.
Concretely, you must create user accounts with unique credentials, and authenticate users before granting them access. Those accounts must only have access to what the user needs to fulfil their role – both in terms of privileges and information – and be password-protected.
By extension, you should only grant administrative privileges and accounts to people who require them. Plus, give them a standard user account for day-to-day work, and make sure they only use their admin privileges when completing administrative tasks, for the reasons discussed earlier.
Furthermore, you must implement MFA where available. For Cloud services, you must always use MFA.
You must also regularly review user accounts and privileges, and remove or disable them when no longer required.
Finally, to meet the Cyber Essentials requirements, you must implement access control on all devices, including mobile devices, and Cloud services holding organisational data.
Practical tips for meeting the Cyber Essentials requirements
As a Cyber Essentials assessor, I’ve guided hundreds of applicants through the certification process. I’ve also advised hundreds of organisations (through our Cyber Essentials Plus packages) on how to meet the requirements more easily.
Here are three tips to simplify meeting the access control requirements of Cyber Essentials:
1. BYOD – use an MDM solution
User-owned devices (BYOD – ‘bring your own device’) that hold organisational data are in scope for the assessment. Managing these devices can be a big challenge for organisations.
To ensure all mobile devices are running on a supported operating system, I recommend investing in an MDM (mobile device management) solution.
With an MDM in place, you can use a conditional access policy to only allow devices running on the latest version of the operating system access to organisational data. This makes managing BYOD devices much simpler.
2. Implement MFA on Cloud services
Again, Cloud services must have MFA enabled. But where the organisation stores data in a lot of Cloud services, this can present a challenge for your assessment.
As an assessor, I need to see the MFA prompt for every Cloud service holding organisational data. This can be very time-consuming and stressful for the applicant.
To simplify the process, implement SSO (single sign-on) where possible.
SSO is an authentication method that enables users to securely authenticate with multiple applications. Microsoft Entra SSO (with Office 365) is compatible with most popular Cloud services.
Suppose an applicant has, say, 30 Cloud services, which are all linked to the SSO solution, such as Microsoft Entra. As an assessor, I’d only need to see the Office 365 admin account and search for the services under Enterprise Apps to get the information I need.
This is much easier and faster than having to individually access each service to view the MFA prompt.
3. Double-check account separation
Again, each employee should have a standard user account, which must be kept separate from admin accounts.
Before your assessment, I strongly recommend checking that you’ve not inadvertently assigned administrative privileges to any standard accounts.
I often see users assigned into a group on AD (Active Directory) with admin privileges who shouldn’t have them. This can happen because those employees require an admin account to carry out their role, but are then mistakenly also given admin privileges on their standard user account.
To check you’ve not made this common mistake, use the command ‘net localgroup administrators’ in CMD (Command Prompt). This will show you a list of users with admin privileges, which you can then check for standard user accounts.
Need more practical Cyber Essentials advice?
Trust a company that has issued more than 7,000 certificates and has received a ‘world class’ NPS (Net Promoter Score) of +100.
IT Governance is one of the founding Cyber Essentials certification bodies and remains one of the largest in the UK.
We can offer practical advice on your Cyber Essentials implementation and/or certification project, as well as more in-depth discussion and additional support.
We first published a version of this blog in November 2022.