Get everyone on the same page – establish a common vocabulary
Risk management lies at the heart of data security. Virtually every best-practice framework and law related to cyber security or data privacy takes a fundamentally risk-based approach, including:
- The UK and EU GDPR (General Data Protection Regulation)
- NIS (Network and Information Systems) Regulations
- DORA (Digital Operational Resilience Act)
- NIST CSF (Cybersecurity Framework)
- ISO 27001
Damian Garcia is our head of GRC (governance, risk and compliance) consultancy. He’s an expert in information security and risk management, with more than 30 years’ experience in the field and an MSc in cyber security risk management.
In this interview, Damian talks us through how to begin managing your cyber security risks.
Next week, we’ll follow up with how to mitigate your risks after you’ve followed the steps below, so keep an eye on our blog!
In this interview
Define ‘risk’
Where do you start with cyber security risk management?
First, I like to think of it as information security risk management. That’s what we [our consultants] do in our job, and makes clearer that security is everyone’s responsibility.
But where to start with risk? Define what the term means to you.
‘Risk’ means different things to different people. Our perception of risk is influenced by:
- Our experiences
- Our background
- Our culture
- Etc.
In business, taking a risk usually means pursuing a business opportunity. A board or senior management is taking a risk on the basis that, if it plays out, there’ll be some kind of upside.
In information security, we normally talk about ‘risk’ to mean some kind of negative outcome for the organisation, if the risk were to materialise.
So, again, be clear on what you and your organisation mean by ‘risk’. Establish a common vocabulary.
Likelihood and impact
So, make sure you’re on the same page about what a ‘risk’ means. For what else in risk management must you establish a common vocabulary?
Most risks have:
- A likelihood or probability; and
- Some form of impact, whether positive or negative.
The question becomes how you quantify and measure both. Your definitions need to be as clear and unambiguous as possible because, again, different people interpret the same words differently.
So, with risk, you might use words like ‘low’, ‘medium’ and ‘high’. You’ve got to define what those terms mean. You need to put those words into context.
Often, when we’re talking about a ‘low’ risk, it means that whatever the effect on the organisation is, you can live with it.
Conversely, at the other end of the scale, a ‘high’ risk means a catastrophic effect. It means you must do something about that risk, because if it materialises, you’d struggle to recover.
Impact categories and values
How do you define the impact of a risk materialising?
The first step is to establish which categories are relevant to the client. Impact categories can include:
- Financial
- Strategic
- Customers
- Employees
- Regulatory
- Operational
- Reputational
Not all categories apply to all organisations. For some businesses, some of these categories may also overlap.
But this list provides a good starting point for a discussion with a client to determine:
- Which of these categories apply to them; and
- Which categories are missing.
How do you define the values to those categories?
That’s another important part of the early conversations with clients – establishing those values. How will the client measure the level of impact? What metrics will you use?
Clearly defining those values is incredibly important. This is how you establish that common language. It’s also how you meet ISO 27001’s requirement for ensuring that repeated risk assessments produce “consistent, valid and comparable results” [Clause 6.1.2.b].
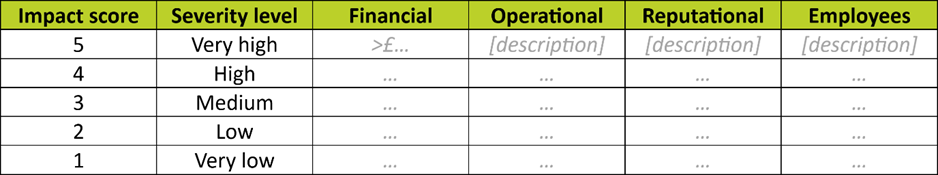
Financial impact is the easiest to define – use figures either in pound sterling [or a different currency] or as a percentage of the organisation’s annual turnover.
What about non-financial impact? Operational or reputational, for example?
Operational impact can look at something like the loss or compromise of a technology or information system that halts your business operations organisation-wide.
The exact impact levels then depend on the duration of the disruption. For example:
- Very low: Halted for hours.
- Low: Halted for a day.
- Medium: Halted for a week.
- High: Halted for multiple weeks.
- Very high: Halted for at least a month.
Reputational impact might look at the level of media interest. For example:
- Very low: Rumours; you might want to clarify the facts informally.
- Low: Minimal interest from local or regional media; you may need to respond informally or formally.
- Medium: Significant interest from local or regional media; formal response required.
- High: Interest from national media; strategic response required.
- Very high: Extensive and sustained interest from national or even international media; continued strategic response required.
Again, the exact values depend on the nature of the organisation – its industry, its size, its risk appetite, and so on.
Why is using many different category types important?
Security is everyone’s responsibility, no matter in what department you work. And not every department can look at the impact in financial terms, so you’ve got to align them to different types of impact.
For example, if you’re a chemical manufacturer, you’ll have someone in charge of health and safety. They need to be able to define impact levels in terms of the number of injuries, disabilities and even fatalities [the ‘employees’ category from the earlier list of impact categories].
When you use a heat map,* the red area [‘high’ risk] is what’s catastrophic to the organisation. But that can be in different terms – even if you can indirectly express non-financial impact in monetary terms.
That’s why you should align the different impact types in a table like this:

Obviously, choose the impact types and complete the blanks as appropriate for your organisation.
[*Heat maps visualise risk severity by combining likelihood and impact levels. We discuss them later in this interview.]
Likelihood categories and values
Do the same principles apply to likelihood categories?
Pretty much. You choose your likelihood scores and give them names:
- Very unlikely
- Unlikely
- Possible
- Likely
- Very likely
Again, make sure you clearly define what each category means, so you’re using that common vocabulary. Different people need to use the same words to mean the same thing.
That means using descriptions, or setting values, like:
- Not expected to occur for years.
- Expected to occur at least annually.
- Expected to occur at least monthly.
- Expected to occur at least weekly.
- Expected to occur at least daily.
How can someone estimate how often something might occur? Just based on past experience?
That’s certainly one way of doing it. It’s also worth checking how often that risk has occurred in the industry.
For example, suppose your organisation has never seen a certain risk materialise, nor – to the best of your knowledge – has anyone else in the industry. You can then reasonably assume it won’t occur for years, and set the likelihood score to ‘1’: very unlikely.
Finding this interview useful? Subscribe to our free
weekly newsletter – the Security Spotlight – to get
future Q&As and other blogs straight to your inbox.
Risk heat map
Where does a likelihood–impact matrix come into the process?
I call it a ‘heat map’. We use it to visualise risks – which risks are catastrophic [red] and require immediate action? Which do you need to monitor [orange]? And which risks can you live with [green]?

When I work with clients, we tend to go for a 3×3 heat map – ‘high’, ‘medium’ and ‘low’ – or a 5×5, which adds ‘very high’ and ‘very low’.
My preference is a 5×5, because if you go for a 3×3, I find that risks tend to aggregate towards the middle – the ‘middle valley’, as I call it. That’s just what happens when people aren’t sure: they tend to go for the middle option.
A different expert recommended to always choose an even number of categories [for risk level], because that forces people to choose between ‘medium/high’ and ‘medium/low’. What are your views?
Well, no two organisations are the same, not least because they’re made up of unique individuals with their own experiences, perceptions and methods. People have their own way of doing things, based on what they’ve found works for them.
I’ve always used odd numbers, which has worked well for me. I can see the reasoning behind using an even number though – you’re forcing people to choose one way or another.
But the key thing is to quantify your risk. You don’t want people to be deciding whether something is risky based on gut feel, but on analysis with hard numbers.
As humans, our assumption of risk – the way we intuitively ‘measure’ risk – is skewed by our perceptions and experiences. But what is intuition and what is hard fact?
As much as possible, you want to analyse your risks based on hard fact.
Yes, it requires a bit more work because it’s more analytical. But when we take a step back and look at the hard figures, it takes the emotion out of it. It helps us make better decisions.
Consistency across the organisation
Different teams are naturally biased towards the risks directly affecting them. Specialist software going down, for example, will be seen as a high-impact incident by a team that depends on it, but low-impact by teams that don’t use it.
Both are perfectly reasonable assessments on a team level. How do you handle such scenarios on an organisational level?
That happens not just at a team level – it can be on an individual level, too.
Within a larger IT team, you might have one specific person responsible for keeping a certain platform or system live. Maybe they even have some kind of bonus plan tied to the availability of that system. So, any failures whatsoever to that system is like the world ending to them, but not to anyone else.
You address individual or departmental bias by taking a holistic approach. The more inputs and opinions you seek, from different parts of the organisation, the more balanced and realistic an overview you’ll get.
So, speak to process owners. Speak to IT. Speak to finance. Speak to HR. And so on.
Learn how to manage your risks
This interview only covered the tip of the iceberg when it comes to cyber security risk management.
To gain an in-depth understanding of how to manage your risks, take our three-day Managing Cyber Security Risk Training Course.
Delivered by an expert practitioner such as Damian, and full of real-life examples, this course gives you the tools to plan and implement a cyber security risk strategy.
Don’t take our word for it
Here’s what our customers say:
Matt:
Good course, instructor had lots of real-world experience and feel like we can start our cyber journey now. Lots of slides in this course!!
Julie:
Great course – as a risk manager I felt I needed to enhance my cyber risk skills and this course definitely helped me do that! Highly recommended.
Stewart:
As an IT Director starting out on how to devise, construct and start down the road of an IT security programme, this was a very helpful course.
It set out the different control frameworks, put them within context of each other and so painted a journey to progress from first steps along the maturity curve. Very helpful in understanding how all the different standards and government advice can fit together.
About Damian Garcia

Damian has worked in the IT sector in the UK and internationally, including for IBM and Microsoft. In his more than 30 years in the industry, he’s helped both private- and public-sector organisations reduce the risks to their on-site and Cloud-based IT environments.
He also has an MSc in cyber security risk management and maintains various professional certifications.
As our head of GRC consultancy, Damian remains deeply committed to safeguarding organisations’ information and IT infrastructures, providing clients with pragmatic advice and support around information security and risk management.
We’ve previously interviewed Damian about the insider threat and common cyber security and ISO 27001 myths.
We hope you enjoyed this edition of our ‘Expert Insight’ series. We’ll be back soon, chatting to another expert within GRC International Group.
If you’d like to get our latest interviews and resources straight to your inbox, subscribe to our free Security Spotlight newsletter.
Alternatively, explore our full index of interviews here.
We first published a version of this blog in October 2022.