Cloud computing is a key tool for organisations, offering a wealth of opportunity to extend IT capabilities and take advantage of innovations.
As more organisations move to remote or hybrid working, Cloud services are more valuable than ever.
However, innovation comes with risk.
In this blog
Security challenges of the Cloud
During the COVID-19 lockdowns, IT teams were under pressure to integrate existing networks with Cloud services, implementing remote-working solutions and technologies hastily.
Further reading: Senior penetration tester Leon Teale gives his top security tips for remote working in this interview.
And as infrastructures become more complex, often in a short space of time, attack surfaces increase and vulnerabilities become more likely. According to Flexera, 89% of organisations now have a multi-Cloud environment.
But Cloud environments are inherently insecure: if you’re allowing access to your data and systems from anywhere with an Internet connection, how do you restrict that access to authorised users only?
Think you understand Cloud security?
Legal and contractual requirements
Organisations must also consider the legal and contractual requirements associated with the Cloud.
In general, organisations are responsible for ensuring the data they collect is protected. That’s irrespective of the data type:
- Confidential business information
- Payment card data
- Personal data
- Etc.
This remains the case even if a third party, such as a Cloud provider, is the one implementing most security controls.
In fact, various standards and frameworks now list explicit Cloud security requirements. This includes ISO 27001:2022, which has a new control for ‘information security for use of Cloud services’.
Further reading: This blog explains the NCSC’s (National Cyber Security Centre) 14 Cloud security principles, which offer solid guidance on what to look for in your provider.
Let’s look at some specific legal and contractual requirements around storing data in the Cloud.
GDPR and international data transfers
In the case of personal data, the UK GDPR (General Data Protection Regulation) doesn’t just make you – the data controller – responsible for protecting that data, but also imposes tight restrictions on transferring it outside the UK (or EEA, in the case of the EU GDPR).
As such, if you store or process personal data in the Cloud, check where the service provider’s physical servers are based. If in a third country – i.e. outside the UK/EEA – you must put adequate safeguards in place.
Further reading: This blog by data privacy trainer and DPO (data protection officer) Andrew Snow explains seven mechanisms you can rely on for transferring personal data internationally.
To ensure you’re meeting your GDPR (and similar) requirements, also ask questions like:
- Since you’re sharing the data, who can access it now? Only your Cloud service provider? Or also sub-processors – third parties your Cloud provider uses?
- If there is a sub-processor, how secure is it and where is it based? If outside the EU/EEA, can you share personal data with it under the GDPR?
- If you delete information on your end, is it really deleted?
Again, with the Cloud, you’re dealing with virtualised servers. Those are often part of huge infrastructures backed up elsewhere. So, carefully review your contracts – ensure adequate provisions are in place.
PCI DSS: outsourcing as an online merchant (SAQ A)
If you’re an e-commerce merchant that outsources your entire e-commerce function, chances are the external party is a SaaS (Software-as-a-Service) or PaaS (Platform-as-a-Service) provider – often with proof of PCI DSS (Payment Card Industry Data Security Standard) compliance.
The SAQ A merchant then tends to think that they only need to manage the service provider relationship, and that’s the end of the story for PCI DSS compliance – but that’s not necessarily true.
Further reading: QSA (Qualified Security Assessor) Stephen Hancock explains common challenges for SAQ A/e-commerce merchants, and how to resolve those challenges, in this blog.
Depending on the model and arrangement, the responsibility may lie with the merchant, service provider, or both.
To establish which applies, make sure you conduct your due diligence – carefully review any contracts or service agreements so you’re clear on your respective responsibilities.
Finding this blog useful? To get notified of future
insights like this, why not subscribe to our free
weekly newsletter: the Security Spotlight?
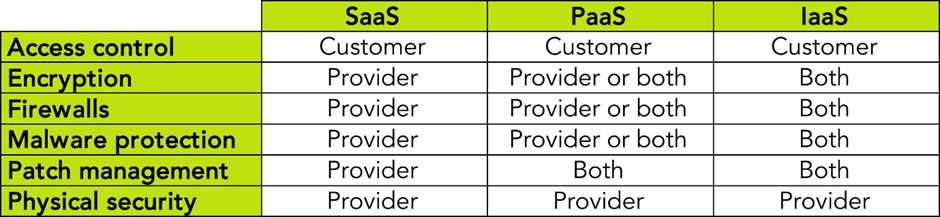
Who’s responsible for what?
A fundamental part of Cloud security is establishing who is responsible for implementing relevant measures. For example:
The table below breaks down typical responsibilities by security control and service type. However, you must check your own contracts and SLAs (service level agreements), as this can differ per provider and service.

Taken from page 3 of our free green paper Cloud Security – Who is responsible?
Cloud service type matters
As the above table shows, the type of Cloud service is a key variable in determining who implements what:
- SaaS generally gives customers the least amount to manage themselves. You’ll largely just need to securely configure the software and conduct due diligence checks.
- PaaS gives customers a bit more work, as they must supply, manage and secure the applications served on the platform. However, the provider manages the underlying Cloud-based platform and infrastructure, on which you must conduct the necessary due diligence.
- IaaS (Infrastructure as a Service) gives customers the most to do in terms of active security management, since you’re supplying your own platform and software. So, you’re fully responsible for securing it. The Cloud provider simply provides the virtual servers and network equipment hosting that infrastructure, which you must check.
How to manage Cloud security
To address your Cloud security risks and responsibilities:
- Establish your requirements; and
- Following a risk assessment, determine what security measures you need to meet those requirements.
For ideas, you could look at the controls listed in general security standards such as ISO 27001, or more Cloud-specific guidance like ISO 27017 or the CSA CCM (Cloud Controls Matrix).
Once you’ve done this, you can list the Cloud services you use (or intend to use), and categorise them by service type: SaaS, PaaS or IaaS.
If at least two types apply, you could present your security measures in a matrix. This gives you a clear overview of:
- What you must manage;
- What your Cloud provider will look after; and
- Where you share the responsibility.
From here, you can form a more detailed implementation plan for the measures you must implement yourself, and add provider-managed controls to your list of due diligence checks.
Boost your credentials
We provide the world’s first formal training in Cloud security to ISO standards.
In our two-day Certified ISO 27017 CIS CCS Training Course, learn how to:
- Interpret Cloud service contracts; and
- Negotiate for security provisions and reporting that works for you.