In the UK, cyber security has been dropping down the board’s list of priorities.
A 2022 Proofpoint study found that 76% of UK board members believed their organisation to be at risk of a material cyber attack in the next 12 months – higher than the global average of 65%.
However, the 2023 edition of that study found that this had dropped to 44% in the UK, whereas the global average had climbed to 73%.
The UK government’s Cyber Security Breaches Survey 2023 confirms this trend.
Fewer directors, trustees and other senior managers of both UK businesses and charities see cyber security as a high priority in 2023 compared to 2022. Specifically, a 13.4% drop for businesses (from 82% to 71%), and a 13.9% drop for charities (from 72% to 62%).
Admittedly, this is just a one-year decline. Nevertheless, it’s a clear trend change.
Let’s look at:
- Possible reasons for this trend change;
- Why it is worrying; and
- Five ways for organisations to improve their security without breaking the bank.
Possible reasons for this trend change
Reasons for organisations deprioritising security may include:
- Rising costs and economic uncertainty;
- Geopolitical tensions and uncertainty; and
- Fewer UK businesses identifying attacks or breaches, according to government data.

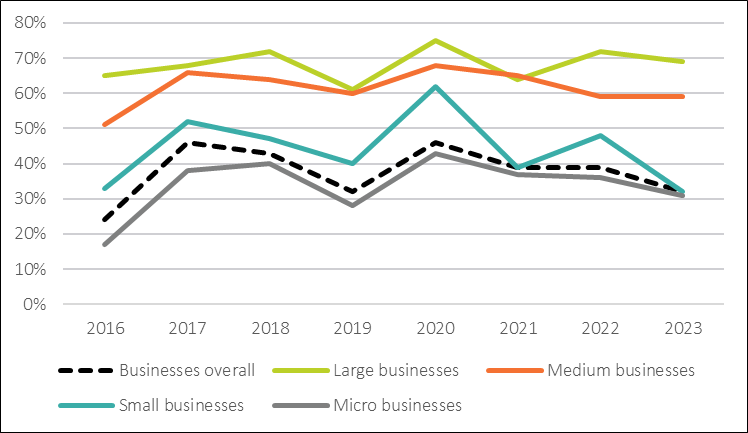
% UK businesses that experienced an attack or a breach in the prior 12 months, according to the UK government’s Cyber Security Breaches Surveys 2016–2023
A hard look at the statistics
The downtrend since 2020, especially for small and micro businesses, may make organisations feel able to cut cyber security spending.
This is a false economy.
1. These are only identified breaches and attacks
According to IBM’s Cost of a Data Breach Report 2023, it takes an average of 204 days (6.7 months) to identify a breach, and only 33% of breaches are identified internally.
So, many organisations will have suffered a breach without being aware of it – yet.
2. Your odds of being attacked are high
Even ignoring point 1, you’re still looking at a roughly one in three chance of suffering an attack or a breach in any 12-month period. That increases to two in three for medium and large businesses.
Those are poor odds.
3. Your odds worsen if you don’t keep up with the latest threats and vulnerabilities
Many attackers use automated tools to find their victims, targeting vulnerabilities rather than organisations.
Even a micro organisation typically holds hundreds of data assets, so is a worthwhile target from an attacker’s perspective. This is even more strongly the case in sectors like finance or healthcare, which hold a lot of sensitive and high-value data.
Furthermore, the average cost of a breach has been increasing over the past five years:

Average cost of a data breach in $, and the year-on-year % changes, according to IBM’s Cost of a Data Breach Reports 2019–2023
The amount of data breached appears to be rising too. Our research found 8.2 billion records breached in 2023. Although it’s only March, 2024 has already exceeded this at 30.2 billion records breached.
Five cost-effective security measures
There are many quick – and cheap – wins where security is concerned. Here are just five of them:
1. Appoint a cyber security manager
By formally assigning security responsibilities to someone who directly reports to the board, you signal to staff that security must be taken seriously.
It also helps ensure your other measures get properly implemented.
2. Implement Cyber Essentials
This government-backed scheme comprises five basic, inexpensive controls that prevent most attacks.
Better yet, small UK organisations achieving certification could receive cyber insurance with a total liability limit of £25,000 – a substantially higher sum than the cost of implementation for most eligible organisations.
Cyber security assessor Ashley Brett provides expert insight into Cyber Essentials in this interview.
3. Conduct vulnerability scanning
Automated vulnerability scanning tools check for missed patches, misconfigurations and other vulnerabilities.
They usually also provide guidance on how to remediate them, and assign a risk rating to each vulnerability, so you can prioritise accordingly.
4. Create policies and procedures
Appropriate documentation is, again, inexpensive, yet vital to any organisation’s security.
Good and properly enforced policies can prove more effective at changing staff behaviour than sophisticated and expensive technological measures.
5. Deploy staff awareness training
Another good way of improving staff behaviour – often the weak link in an organisation’s security – is to roll out staff awareness training.
This needn’t cost much or take up much time, particularly with options like elearning available.
Suffered an incident?
Get FREE expert insight from Cliff Martin, head of incident response at our sister company GRCI Law, into:
- Defence in depth, with prevention, detection and response;
- Cyber incident response plans;
- The different stages of incident response;
- Staff training;
- Internal expertise vs outsourcing;
- Incident responder skills; and
- Much more!
Security Spotlight
To get news of the latest data breaches and cyber attacks straight to your inbox, subscribe to our free weekly newsletter: the Security Spotlight.
Every Tuesday, you’ll get a short email with:
- Industry news, including a round-up of the week’s publicly disclosed data breaches and cyber attacks in Europe;
- Our latest research and statistics;
- Interviews with our experts, sharing their insights and expertise;
- Free useful resources; and
- Upcoming webinars.